In today’s digital world, protecting data and accounts is becoming more important than ever. Especially in the realm of web applications, managing access rights and user authentication is an integral part. IP Authentication is one of the common methods used to control access to systems and online services. In this article, we will learn about what IP Authentication is and how to use it effectively.
What is IP Authentication?
IP Authentication is a user authentication method based on their IP address. Instead of using usernames and passwords, IP Authentication uses information about IP addresses to determine access rights to the system.
In IP Authentication, rules and configurations are set up to only allow specific IP addresses to access the service or system. IP addresses not included in the allowed list will be denied access.
IP Authentication helps enhance security by limiting access rights only to trusted IP addresses. This helps prevent attacks from external sources and protects important data from intrusion.
Key Benefits of IP Authentication
IP Authentication brings many significant benefits, especially in protecting your system and data. Here are some important benefits of IP Authentication:
Higher Security
IP Authentication enhances security by only allowing authorized IP addresses to access the system. This helps prevent attacks from external sources and minimizes the risk of unauthorized access.
Access Control
By specifying specific IP addresses allowed to access, this authentication helps you accurately control who can access your system. This is particularly useful in managing access rights for employees and partners.
Easy Deployment and Management
IP Authentication is an easy-to-deploy and manage method. You just need to configure the server and firewall to only allow connections from these IP addresses and regularly monitor this list to update.
Reduced Risk from Brute Force Attacks
IP Authentication can reduce the risk from brute force attacks, where attackers try to guess passwords by attempting a series of different usernames and passwords. By eliminating access from unauthorized IP addresses, IP Authentication makes brute force attacks more difficult.
Increased Flexibility
IP Authentication provides flexibility in access management, allowing you to easily add or remove IP addresses from the allowed list depending on the needs and requirements of the system.
Guide to IP Authentication for Proxyv6
Step 1
Step 2
Step 3
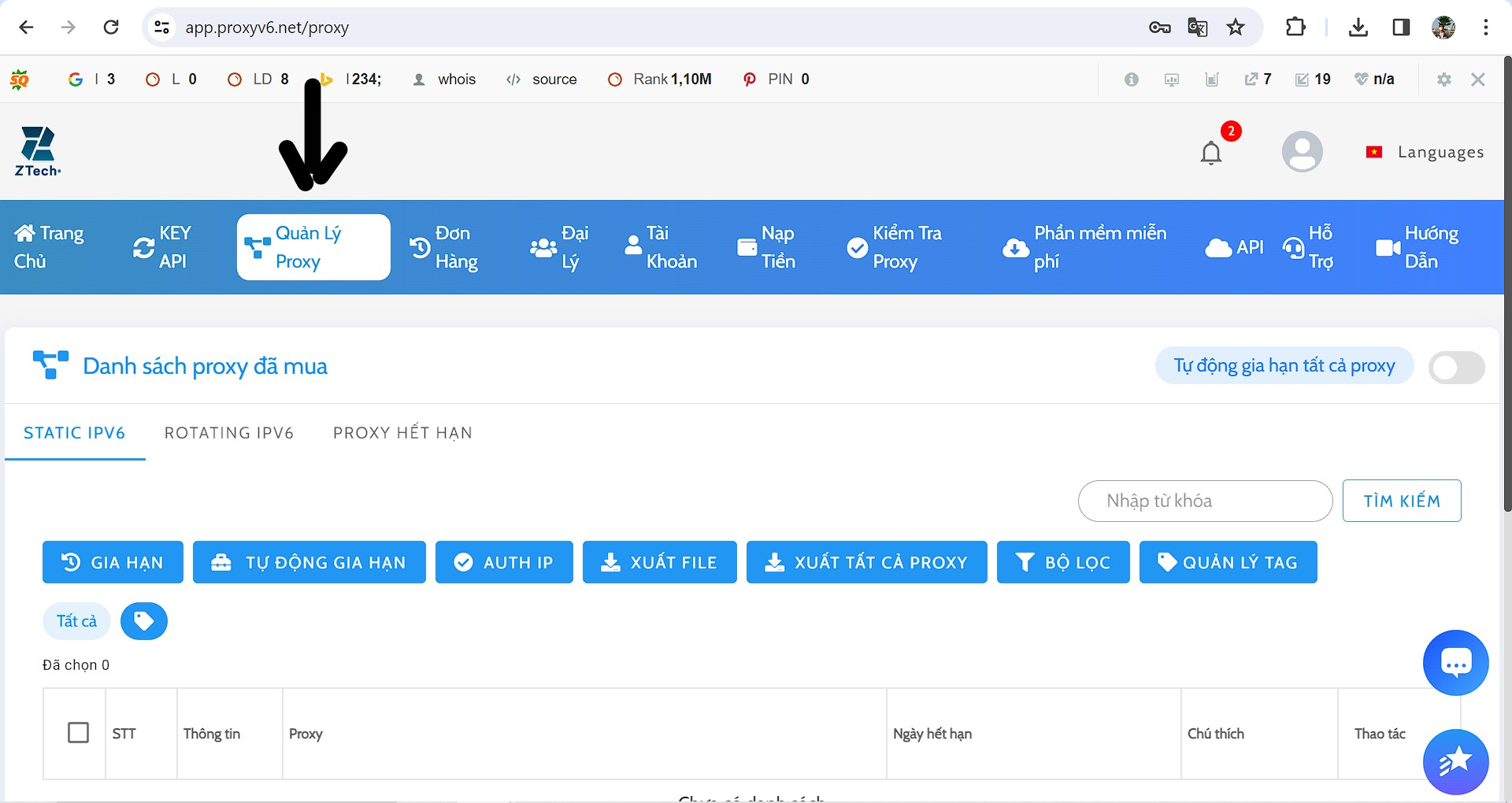
Step 4
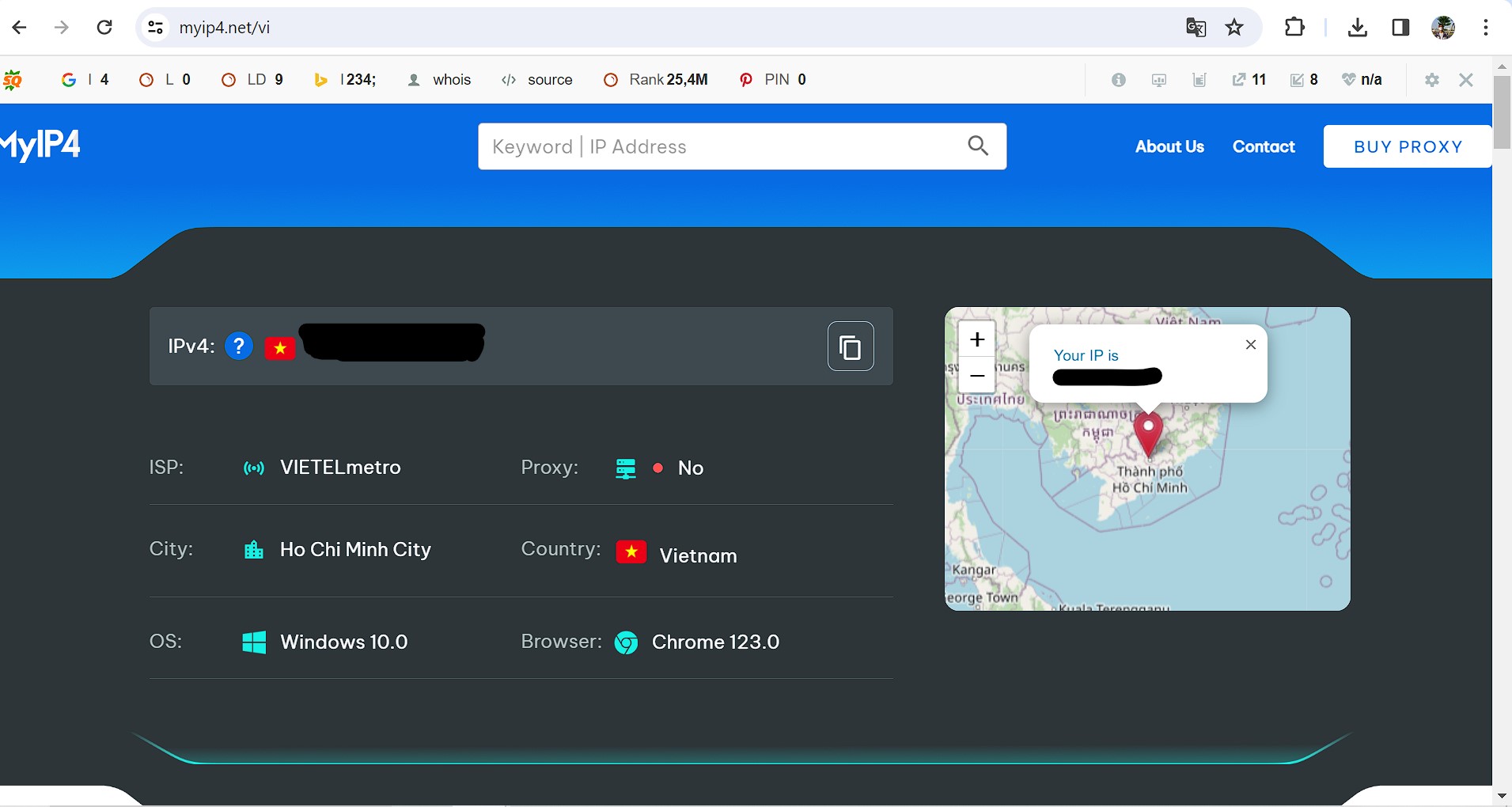
Step 5
Buy Cheap Proxies at Proxyv6.net
To achieve optimal performance in your SEO tool usage strategy, using proxies is an important means, and Proxyv6.net is a reliable address to buy cheap proxies. With a powerful and diverse proxy team, Proxyv6.net provides high-quality proxies, from basic proxies for daily needs to advanced proxies for large projects.
Using proxies not only helps protect online identity but also helps safely and effectively research keywords and track keyword positions. Don’t overlook in your SEO strategy, experience the service of buying cheap proxies at Proxyv6.net to ensure stability and security in optimizing your website.