In today’s digital age, protecting online information is not just a requirement but a vital necessity. With the rapid development of technology, cyber threats are becoming increasingly complex. That’s why understanding cyber security, or network security, and the most common types of defenses is extremely important. In this article, we will explore what Cyber Security is and specifically the top 5 most common types of cyber security in 2024.
Understanding Cyber Security
What is Cyber Security?
Cyber Security, also known as network security, is a crucial field in information technology and telecommunications, focusing on protecting computer systems, data, networks, and online-connected devices from threats, attacks, and unauthorized use. The primary goal of cyber security is to ensure the confidentiality, integrity, and availability of information on the network.
Cyber Security not only involves implementing measures and technologies to prevent, detect, and respond to network attacks but also relates to building policies, procedures, and user education to enhance awareness of network security and safe IT usage habits.
In the context of rapidly developing digital environments, cyber security-related threats are increasingly complex and diverse, ranging from malware, sophisticated network attacks to data theft and intrusions into the network systems of organizations and individuals. Therefore, the role of cyber security becomes increasingly important in protecting online information and data.
The Functions of Cyber Security
Cyber Security has many important and necessary functions in today’s digital world, including:
Protecting Critical Data
Cyber Security ensures that the critical data of individuals, organizations, and businesses are protected from unauthorized access, loss, or destruction.
Preventing Network Attacks
Cyber Security provides measures and technologies to detect, prevent, and respond to network attacks such as viruses, malware, denial-of-service attacks (DDoS), and intrusions into systems.
Protecting Privacy
Cyber Security ensures that personal information and user privacy on the network are protected, preventing unauthorized access and disclosure of personal information.
Ensuring Availability
Cyber Security ensures that online systems, services, and applications are always available and functioning normally, avoiding attacks causing disruptions or downtime.
Protecting Reputation and Trust
Cyber Security helps prevent attacks targeting the reputation and trust of organizations, businesses, or individuals online, from website attacks to system intrusions and online reputation damage.
Compliance with Regulations and Laws
Cyber Security helps organizations and businesses comply with regulations and laws related to information and data protection, minimizing legal risks and avoiding negative consequences from violating network security regulations.
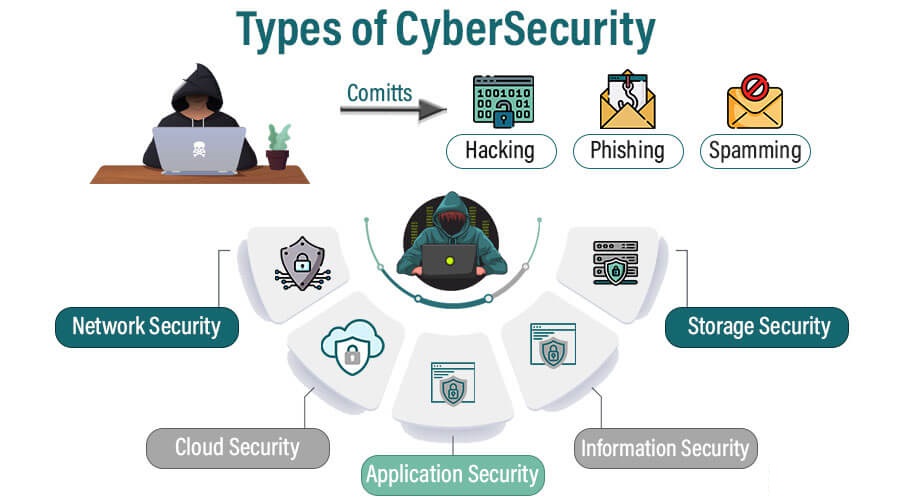
Top 5 Most Common Types of Cyber Security in 2024
In 2024, the top 5 most common types of cyber security include:
Network Security
Focuses on protecting network systems from unauthorized access, network attacks, and other threats. Common network security measures include firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and virtual private networks (VPNs).
Application Security
Focuses on protecting software applications from security vulnerabilities and network attacks. Common application security measures include source code review, penetration testing, and data encryption.
Data Security
Focuses on protecting data from unauthorized access, misuse, disclosure, or destruction. Common data security measures include data encryption, data backup, and access control.
Cloud Security
Focuses on protecting data and applications stored on cloud computing platforms. Common cloud security measures include data encryption, access control, identity and access management (IAM).
Mobile Security
Focuses on protecting mobile devices from network attacks and other threats. Common mobile security measures include password protection, data encryption, and using mobile security apps.
Buying Cheap Proxies at proxyv6.net
If you’re looking for a cheap proxy service, then proxyv6.net is worth considering. Proxies are essential tools in many online activities, from enhancing security to data collection. Proxyv6.net offers a range of proxies at reasonable prices, helping you save costs while ensuring quality and performance.
With cheap proxies from proxyv6.net, you can experience stable connections and high access speeds. This service caters not only to individual needs but also to businesses and IT professionals. Additionally, proxyv6.net regularly updates its proxy list to ensure flexibility and safety for users.
With a cheap proxy service like proxyv6.net, you can take advantage of the features and benefits of proxies without impacting your budget. Explore the advantages that proxyv6.net offers and leverage the benefits of using proxies in your online activities.