In today’s cyber world, cyber attacks are becoming increasingly common and causing many serious problems for individuals, organizations and online businesses. One of the most worrying types of attacks is DDoS attacks. In this article, we will learn about what DDoS is, how it works, common types of attacks, and the distinction between DoS and DDoS.
What is a DDoS attack?
DDoS (short for Distributed Denial of Service) is a type of cyber attack whose main goal is to make a system, server or online service unavailable to legitimate users by creating a large number of requests or messages from many different sources.

DDoS là gì? Cách phân biệt giữa DoS và DDoS
How DDoS works?
DDoS attacks are often carried out by combining the power of multiple connected devices into a single target, creating enough pressure to overload a system or service, making it untraceable. access or cause serious disruption.
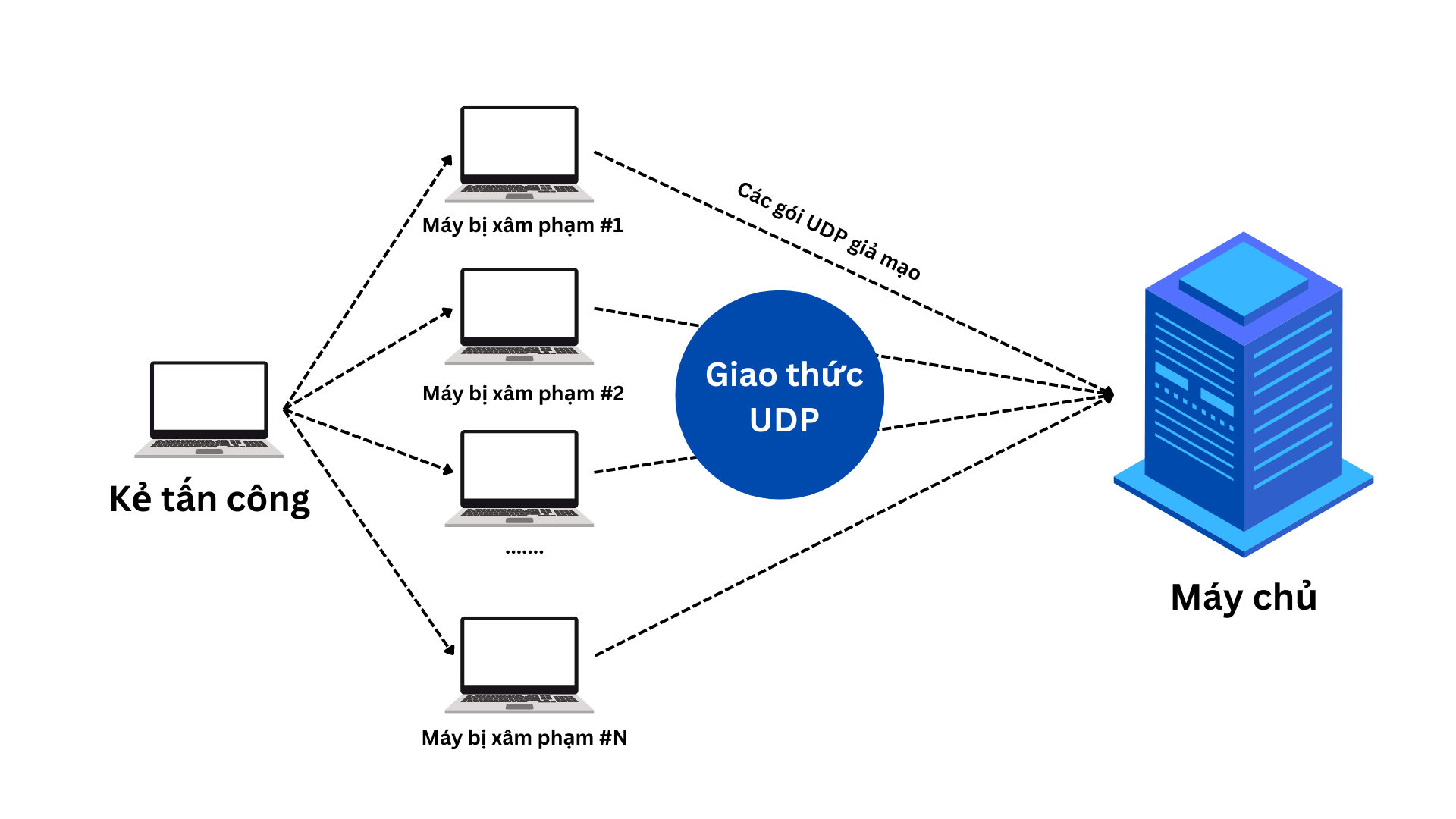
A DDoS typically uses botnets, a network of devices (usually personal computers or IoT devices) that have been infected with malware and controlled remotely by the attacker. Devices in this botnet act as “perpetrators” in the attack, sending thousands or even millions of requests to the target at the same time.
When the target system or server has to handle this large number of requests, it can become overloaded, leading to reduced performance or complete shutdown.
DDoS is one of the most dangerous forms of cyber attack and can cause many serious problems, including lost revenue, damaged reputation, and economic damage to organizations and individuals. being attacked.
To protect against DDoS attacks, system administrators and organizations need to deploy strong network security measures, such as firewalls and network monitoring, to detect and prevent these attacks.
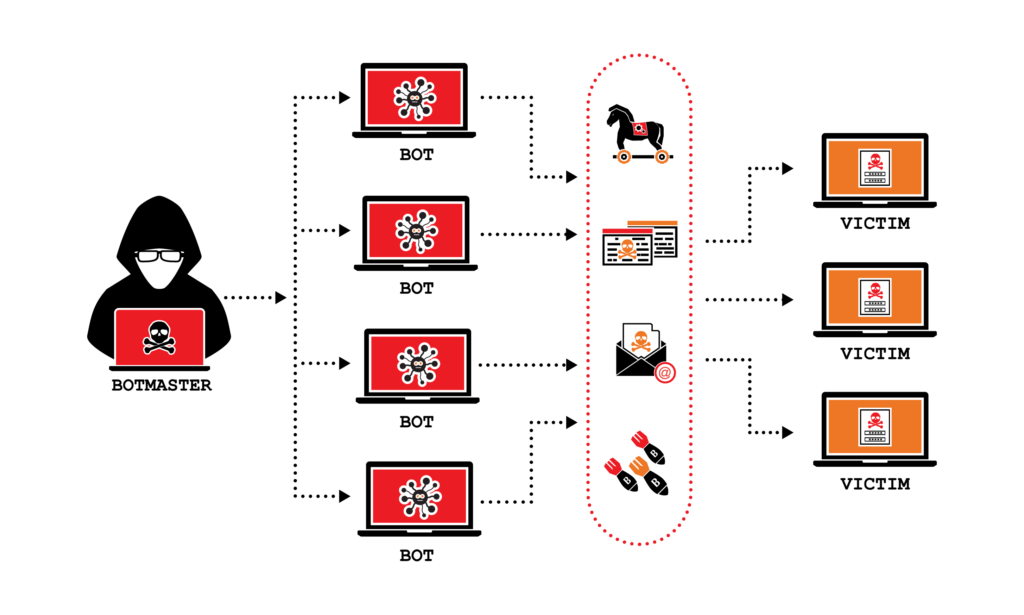
How to distinguish between DoS and DDoS attacks?
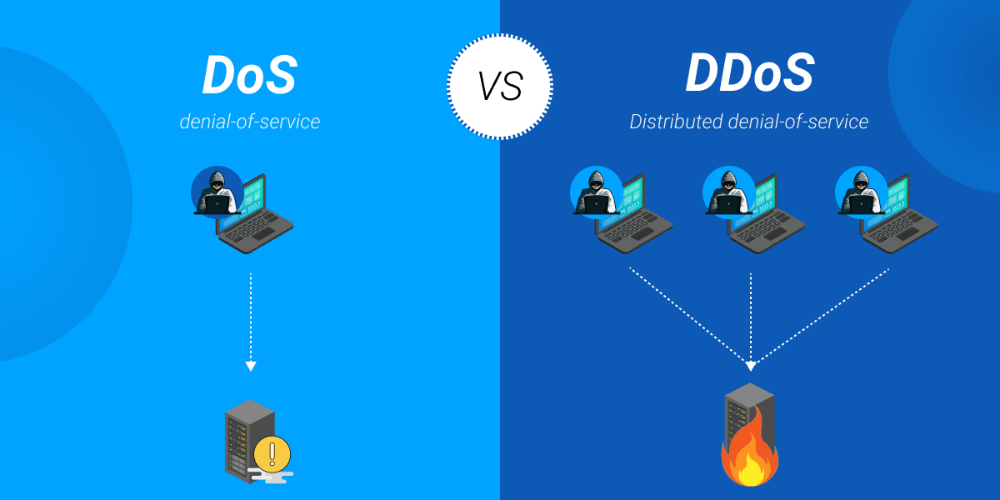
DoS and DDoS are two different types of cyber attacks. DoS stands for “Denial of Service”, while DDoS stands for “Distributed Denial of Service”. Here are some important differences between them:
Differences in scale
- In a DoS attack, only a single system or device is used to attack the target.
- In a DDoS attack, multiple systems or devices participate in the attack simultaneously.
Dispersion
- DoS attacks focus on attacking from a single source.
- DDoS attacks use many different sources to send requests, making it more difficult to prevent and counter the attack.
Speed Attack
- DoS attacks are usually slower than DDoS attacks.
- DDoS attacks are faster than DoS attacks due to the contribution of multiple devices.
Difficulty in blocking
- A DoS attack can be blocked more easily because it uses a single source.
- DDoS attacks are difficult to prevent because many devices send packets and attack from multiple locations.
The track
- DoS attacks are usually easy to track because they are carried out from a fixed source.
- DDoS attacks are difficult to track because they come from many different sources around the world.
Attack type
- Types of DoS attacks include buffer overflow attacks, Ping of Death or ICMP flood attacks, and Teardrop Attacks.
- Types of DDoS attacks include Volumetric attack (bandwidth attack), Fragmentation Attack (data fragmentation) and Application Layer Attack (exploiting vulnerabilities in applications).
Forms of DDoS attacks
ICMP Flooding attack
This type of attack focuses on sending fake ICMP (Internet Control Message Protocol) packets or large packets, overloading the network’s bandwidth and making the service unavailable.
SYN/ACK Flooding attack
This attack uses sending multiple TCP connection requests without completing connection establishment, resulting in system resource consumption and service interruption.
UDP Flooding attack
UDP (User Datagram Protocol) packets are sent to the destination server without previously establishing a connection, creating great pressure on the system.
UDP Flooding Attack
DNS Amplification attack
This attack uses DNS requests with a spoofed source address, causing the DNS server to respond with a large amount of data to the spoofed address, overloading the target system.
Buy cheap proxies at proxyv6.net
If you’re looking for powerful and economical proxy solutions, you can’t go wrong with proxyv6.net. This is a platform that provides quality proxy services at reasonable prices, suitable for the needs of both individuals and organizations.
Proxyv6.net offers a wide range of proxy packages at competitive prices. You can choose between options to suit your needs, from personal plans for individual users to business plans for large organizations. This flexibility helps meet the needs of everyone, from people using proxies to browse anonymously to businesses that need proxies to manage multiple online accounts.
With proxyv6.net, you will get powerful IPv6 proxies, ensuring stability and high connection speed. This is especially important for users who need proxies to perform online activities efficiently and quickly.